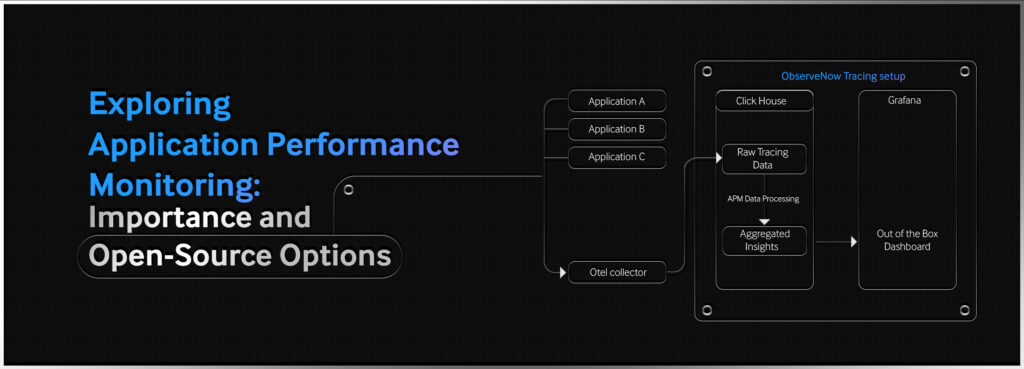
KubeCon + CloudNativeCon North America 2022 was my first experience attending a conference entirely dedicated to the latest trends and technologies evolving within the Kubernetes ecosystem. As I approach nearly a year of working with CNCF open source tools such as Backstage, Prometheus, and Argo used by OpsVerse to build a unique k8s dev toolbox, it was both humbling and exciting to see the various products this year built entirely using CNCF projects. Equally as remarkable were the new advancements being made to accommodate the ever-growing use cases for customers transitioning their legacy infrastructures to k8s and the cloud.
With the next edition of KubeCon + CloudNativeCon Europe around the corner, here are my summaries of a few sessions that caught my attention while attending the live conference and browsing the seemingly endless list of post-event recorded sessions and workshops:
Armoring Cloud Native Workloads with LSM Superpowers
Speaker: Barun Acharya, Software Engineer, Accuknox
The talk described the process of implementing container security during runtime. An online search for the top problems faced while using Kubernetes revealed that the learning curve and complexity of the Kubernetes architecture were among the top two across multiple sources. In order to solve the commonly faced problems associated with container-level security, storage, and networking in k8s, a careful configuration of security policies is required. Coupled with the challenge of a steep-learning curve, however, doing so can result in the compromise of sensitive data via potential oversights. A feasible open source solution to help tackle this issue can be implemented using KubeArmor’s container runtime security features which help detect potential security risks with respect to confidential information.
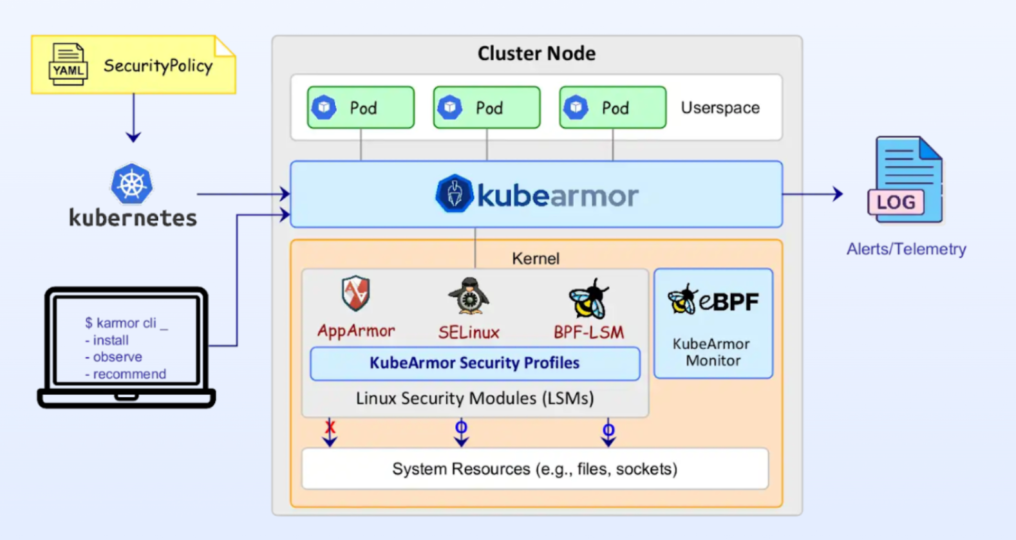
Source: KubeArmor, AccuKnox
Kubernet-Bees: How Bees Solve Problems of Distributed Systems
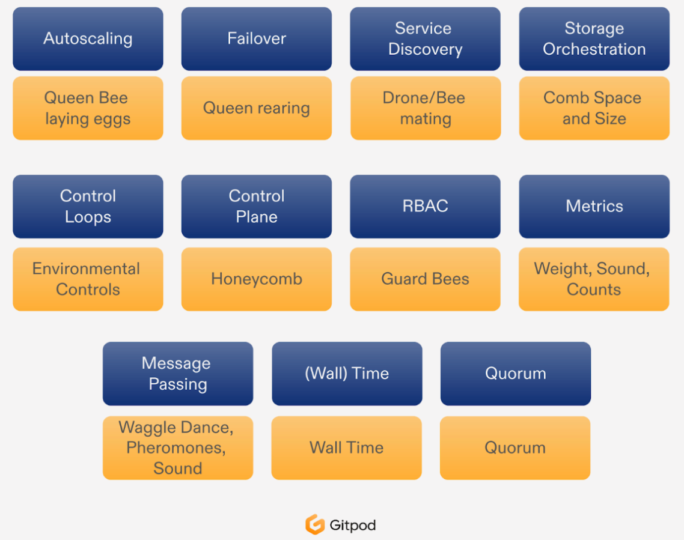
Source: Gitpod
Speakers: Christian Weichel, Chief Technology Officer, Gitpod, Simon Emms, Senior Engineer, Gitpod
Kubernet-Bees was a discussion held by the GitPod team that addressed the viability of using distributed systems to create open source dev environments that can be easily integrated with GitHub or other existing codebases without having to set up local dependencies. The ease of use compared to setting up dependencies locally for different projects was also covered, with the presentation being centered around an interesting analogy to the behavior of bees and designation of their roles within the hive, in order to explain the software process. In my opinion, it’s cool that it pretty much includes all dependencies and significantly helps save time by avoiding the common installation errors faced while setting up dependencies, especially Node modules, for frontend projects.
How To Handle Node Shutdown in Kubernetes
Speakers: Xing Yang, Tech Lead, VMware Ashutosh Kumar, Senior Member of Technical Staff, VMware
The talk by Ashutosh Kumar and Xing Yang, from VMWare, gave a thorough introduction to the node shutdown process and the circumstances surrounding the two main types of node shutdown: graceful and non-graceful. Some of the events cited in the presentation to be the common causes behind node shutdowns were: hardware failure, reboot due to a security patch, displacement of short-lived cloud compute instances etc. Since node shutdowns can not only result in pod eviction and data loss for the local services, but also have a cascading effect on other nodes residing in the same cluster, it is imperative that the configurations in place allow for a graceful shutdown of the node, resulting in enough provisioned time and resources for the containers to shut down with minimal data loss. 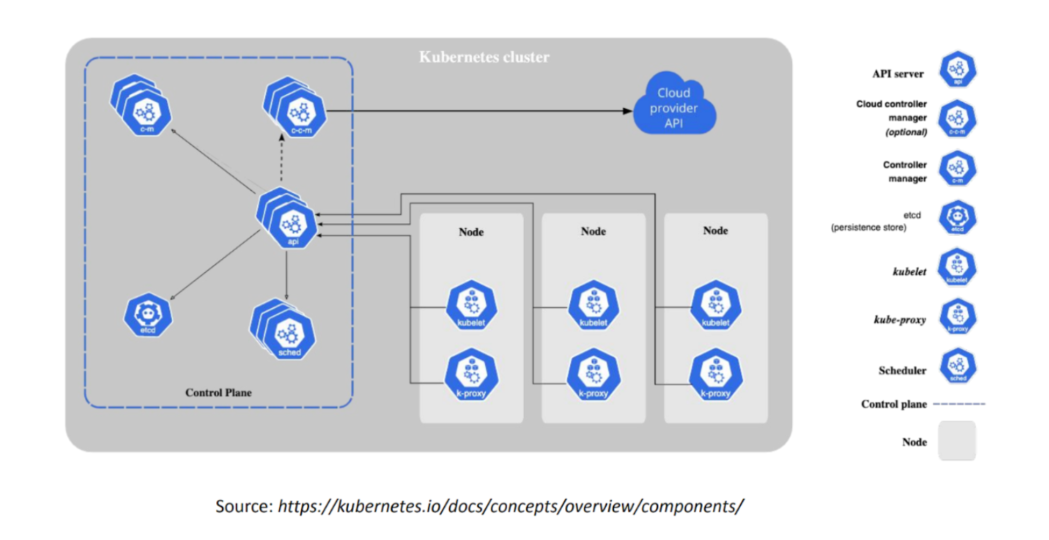
Untrusted Execution: Attacking the Cloud Native Supply Chain
Speaker: Andrew Martin, CEO, Control Plane
This presentation by Andrew Martin of Control Plane delved into the concept of supply chain security, through an initial overview of the supply chain process and the susceptibilities that enable malicious attacks to cause severe damages. He provided the procedures and action items commonly used by bad actors to infect and exploit a supply chain, some of them being: infect a trusted supplier’s trusted packages, infect the source code using exposed secrets and keys, infect the build infrastructure. The consequences of such compromises can usually lead to advanced persistent threats, commercial espionage/reputation damage, theft of IP and data, compromise of secrets, cryptojacking, to name a few. Control Plane’s approach to handling this pervasive issue is through the implementation of a systematic process called threat modeling, which helps improve transparency and detect threats early in the security attack. 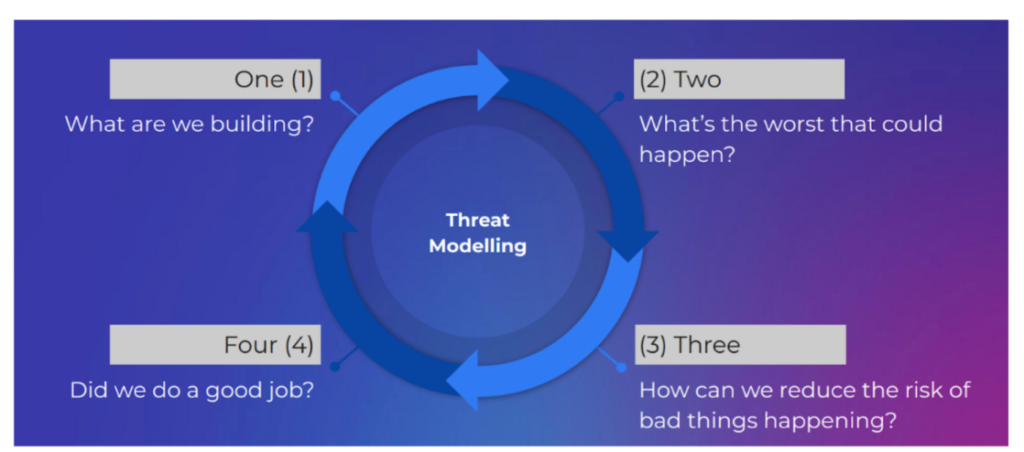 Catalog of supply chain compromises: https://github.com/cncf/tag-security/tree/main/supply-chain-security/compromises Overall, attending the conference as a beginner in the DevOps field was a great learning experience as I had the opportunity to easily pick the sessions that I found the most interesting—a convenience thanks to the virtualization of the event. Considering that the rest of our team in the U.S. attended the event in-person, I’m also looking forward to physically attending next year’s event as I’m sure it’ll add an extra layer of engagement that you can’t get virtually. OpsVerse is a fully managed DevOps tools platform that enables companies to deploy and start using DevOps tools within minutes. The tools can be deployed as private SaaS or in any public cloud or region
Catalog of supply chain compromises: https://github.com/cncf/tag-security/tree/main/supply-chain-security/compromises Overall, attending the conference as a beginner in the DevOps field was a great learning experience as I had the opportunity to easily pick the sessions that I found the most interesting—a convenience thanks to the virtualization of the event. Considering that the rest of our team in the U.S. attended the event in-person, I’m also looking forward to physically attending next year’s event as I’m sure it’ll add an extra layer of engagement that you can’t get virtually. OpsVerse is a fully managed DevOps tools platform that enables companies to deploy and start using DevOps tools within minutes. The tools can be deployed as private SaaS or in any public cloud or region